Key Takeaways
- CMMC is a cybersecurity maturity model tailored for Department of Defense (DoD) third-party contractors. It builds upon existing regulations like DFARS and NIST 800-171.
- Final rulemaking for CMMC was completed in September 2025 and the DoD will begin a phased rollout of CMMC requirements as a condition for contracts beginning in November 2025.
- Taking action now to align with CMMC standards is essential for organizations seeking to work with the DoD and handle sensitive information securely.
The Cybersecurity Maturity Model Certification (CMMC) program provides a structured approach to assessing whether defense contractors meet the Department of Defense (DoD) security standards for safeguarding sensitive information.
As of September 2025, CMMC compliance is no longer optional. It directly determines contractors’ ability to win or retain DoD contracts.
The DoD will implement the program in phases over the next three years:
- Phase 1 (November 10, 2025): Solicitations will require CMMC Level 1 or Level 2 self-assessments. DoD may also, at its discretion, require third-party CMMC Level 2 assessments in this phase.
- Phase 2 (November 2026): Applicable solicitations will require third-party CMMC Level 2 assessments.
- Phase 3 (November 2027): Applicable solicitations will require CMMC Level 3 assessments performed by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
- Full Implementation (November 10, 2028): All DoD contracts and solicitations will include the required CMMC level as a condition of award.
- CMMC is here, and action is required to avoid delays and lost opportunities. Take our CMMC Readiness Assessment Quiz to see if you’re on the right path for compliance.
Understanding the CMMC Framework
CMMC is an information security maturity model designed specifically for DoD third-party contractors, building upon existing regulations like DFARS and NIST 800-171. The goal is to ensure comprehensive security across the DoD supply chain.
Any contractor engaged with or seeking a contract with the DoD must obtain a CMMC. This applies to all tiers of the supply chain, including small businesses, commercial item contractors, and foreign suppliers.
Under CMMC, companies handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) must achieve one of the three CMMC levels, as detailed in their contracts, to qualify for defense-related projects.
Two types of data are addressed within CMMC:
- FCI: Non-public information provided by or created for the government under a contract for developing or delivering a product or service.
- CUI: Data requiring protection or restricted dissemination according to federal laws, regulations, and government-wide policies.
CMMC does not alter existing cybersecurity requirements for protecting FCI and CUI but rather strengthens the enforcement of existing security standards.
CMMC Maturity Levels Explained
CMMC defines three maturity levels that DOD contractors may be required to meet. The appropriate level for an organization depends on the sensitivity of the DoD information it handles.
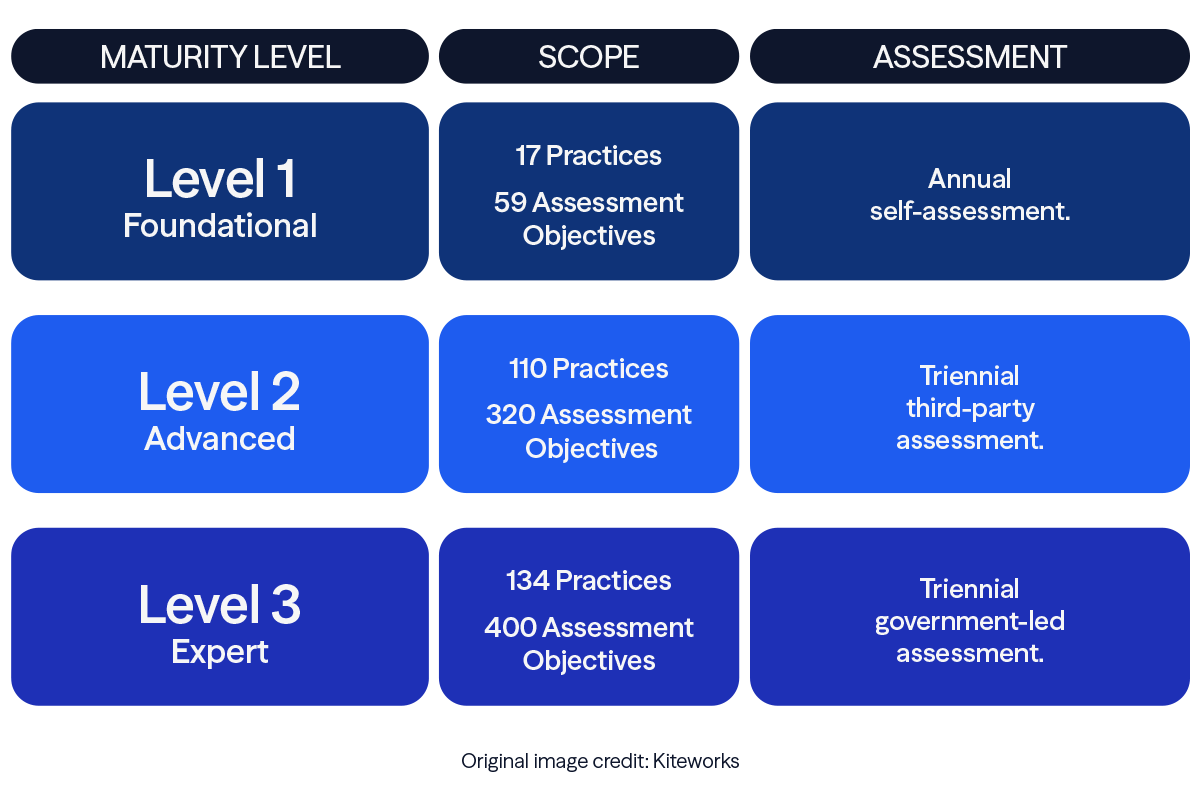
Level 1
Applicable to organizations working with FCI only. These organizations must focus on basic cyber hygiene and adhere to the practices outlined in FAR 52.204-21.
Level 2
Designed for organizations handling CUI. These organizations must comply with the 110 security practices and 320 assessment objectives specified in NIST 800-171.
Level 3
Reserved for organizations handling CUI and exposed to Advanced Persistent Threats. These organizations must demonstrate advanced cybersecurity capabilities in line with NIST 800-172.
Steps to Prepare for CMMC Compliance
Preparing for CMMC compliance involves several key steps:
1. Conduct Discovery Activities
Begin by assessing your current cybersecurity posture:
- Locate all assets: Inventory your organization's hardware, software, and data.
- Map data flows: Trace how FCI and CUI move through your systems.
- Understand existing controls: Review current security controls and practices to identify strengths and weaknesses.
2. Determine CMMC Scope
Define the scope of your CMMC efforts:
- Identify covered assets: Determine which parts of your organization handle FCI and CUI.
- Segment systems: Isolate critical areas from other parts of your network to minimize compliance scope.
- Document boundaries: Clearly outline the scope of your CMMC efforts to ensure all relevant components are included.
3. Perform Gap Assessment
Execute a thorough gap assessment to compare your current cybersecurity practices with CMMC requirements:
- Review maturity levels: Identify the CMMC level required based on your contract requirements.
- Assess existing controls: Evaluate your current controls against the CMMC practices for your target maturity level.
- Identify gaps: Highlight where your current practices do not meet the required standards.
- A CMMC Readiness Review measures your current compliance state and assesses the effectiveness of existing security procedures. Take our CMMC Readiness Quiz to get started.
4. Develop Roadmap & Action Plan
Create a comprehensive action plan to address identified gaps:
- Prioritize tasks: Determine the order in which gaps should be addressed based on risk and resource availability.
- Set milestones: Establish KPIs to monitor progress.
- Allocate resources: Assign the necessary resources, including personnel, budget, and time, to ensure successful implementation.
5. Remediate Identified Gaps
Begin remediation efforts to close the identified gaps and enhance your cybersecurity posture:
- Implement security controls: Deploy necessary controls and technologies to meet CMMC requirements.
- Update policies and procedures: Revise or create policies and procedures to align with CMMC standards.
- Conduct training: Provide education to ensure staff members understand and can effectively implement new security measures.
- Perform continuous monitoring: Establish ongoing monitoring and assessment to maintain compliance and address new vulnerabilities.
Although anyone can conduct a gap assessment, the expertise of your reviewer can impact your success in a CMMC audit. To ensure a thorough evaluation, consider working with a Registered Practitioner Organization (RPO). RPOs, designated by the CMMC Accreditation Body (Cyber AB), possess an understanding of CMMC standards and are recommended to guide contractors through the preparation process.
As a Registered Practitioner Organization (RPO), Eide Bailly can support CMMC readiness for both Level 1 and Level 2. We are also a Certified Third-Party Assessor Organization (C3PAO) authorized to perform Level 2 assessments. It should be noted that the same firm cannot support both CMMC preparedness and conduct assessments, and our team has established trusted partnerships to support clients throughout this process. Our team can help you prepare, validate compliance, and position your organization for continued eligibility in the defense supply chain.
Next Steps Toward CMMC Compliance
Phased implementation of CMMC requirements has begun. Taking proactive steps now is essential for organizations seeking to work with the DoD and handle sensitive information securely.
By understanding your required level, assessing your current security posture, and addressing gaps in line with CMMC standards, you can position your organization for future contract eligibility.
Not sure where to begin? Take our CMMC Readiness Assessment to gauge your organization’s preparedness and identify areas for improvement.
Minimize Risk and Maintain Compliance

Risk Advisory Services
Who We Are
Eide Bailly is a CPA firm bringing practical expertise in tax, audit, and advisory to help you perform, protect, and prosper with confidence.




